
Have you ever wondered what if your iPhone’s security is compromised and someone is accessing your iPhone remotely? There are various incidents when iPhone security is compromised and users do not even know that it is happening. Although the iPhone provides state-of-the-art security features, in this technological world, anything can happen to anyone at any time.
The reason why Apple is so secure is because of its closed development as well as its operating system security features. But still, chances are there which indicates that your phone security can be breached by any hacker trying to gain access to your data and information. Then how to tell if someone is accessing your iPhone Security? We will help you out here!
Earlier, there were many incidents where the security features did have a loop, creating a chance for hackers to crack their firewall and control a user’s phone. Hackers might get your personal photos, videos, bank information, email ID passwords, and data alongside using it for their gain without being caught. If you are an iPhone user, you need to stay ahead with the technology and do whatever you can in your capacity to be safe. This article brings you different ways of ensuring that your phone is safe and that someone is not remotely accessing it.
- The first thing you should do is check your devices after signing into your Apple account.
- After signing in, check devices from settings which will show the devices menu.
- If you observe a device that is unknown to you, remove it as soon as possible since it can be a foreign device that can be accessing your device remotely.
Remote Access Mechanism for iPhones
Understanding the remote access mechanisms is important for an iPhone user. Whenever your iPhone is under remote access, you need to check for the signs. These signs might be observed in the following aspects.
1. Notifications
Different unexpected notifications might be coming from different sources or applications that you are not using or do not know about. Readers must be alert in case they are receiving such notifications, especially from those apps that they are not using or have not downloaded.
2. Password Changes
It is another important alert which is faced by users that their security was breached and passwords were being changed by remote access. Unexpected password change indicates an intrusion from an external source which is important to control on the spot to avoid any damage. It is integral to thoroughly secure all your passwords and later on, look into the device from an investigative perspective to detect where the actual problem lies.
3. Operational Mess
Sometimes, the phone is not working optimally because of low usage from the user’s end. The reason is obvious that someone else is utilizing your whole phone energy which is important to cater as soon as possible. Unexpected shutdowns, excessive data usage, and frequent crashes are important to notice since these unusual behaviors indicate something fishy, mostly resulting in authorized access which is accessing your device’s security.
4. Low Performance
In case of systematic hack or remote access, the performance of the phone decreases quickly such as the device faces lags, delays, and slow processing. However, the iPhone is considered the best phone due to its speed and user experience. Please look out for app optimization and check battery health first, if both things are working fine, it could be a hint that some unauthorized application is making your system slow due to their external control.
5. Unexpected Heating and Battery Drain
Although iPhones were considered battery-eating smartphones by a few people since there were different models where the battery was not performing up to the mark those problems were solved earlier. There are no such battery drainage and device heating problems. If someone is facing these issues without excessively using the smartphone, then it is an indication that at the backend, someone else is consuming the device battery due to unauthorized access or there might be software that is impacting the overall performance of the battery due to exporting data.
6. Denial of Access
In some cases, it is reported by the users that different sites are restricted although the same sites are working perfectly on their colleagues’ or peers’ devices. It is because of geographical location that if your phone is hacked by an external resource, they might be operating the device from another location, or due to compromised security, the applications or sites are not taking any sort of command from your device, indicating that you need to check your phone for any potential danger.
Ways to tell if Somone is Accessing Your iPhone
There are different methods for checking whether your iPhone is remotely accessed or not. Among these methods, the top two methods are discussed in detail below.
Signed-in Devices Check
In this case, the users can check different connected devices with their Apple ID. By navigating through the settings, a list appears that displays a clear picture of familiar and unfamiliar devices where you can test whether your device is remotely accessed or not.
Removal of Unrecognized Devices
If there is one or more than one device appearing on your list of signed-in devices, it is important to remove them as soon as possible since these are not your registered logins and it is an indication that someone is trying to access your iPhone without your knowledge. Always keep on checking this list to stay safe.
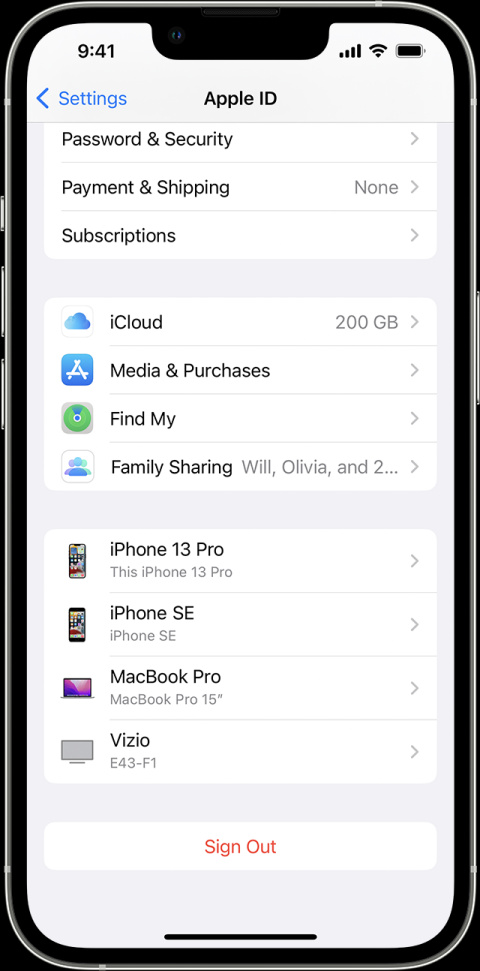
How to remove a device from Apple ID on iPhone
- Login with your Apple ID
- Select unrecognized devices
- Tap the device in the list
- Click on Remove from the account
Security Features Check
Among these questions, it is important to know how can a user keep a check on the security since it is not feasible for everyone to do this thing daily. The following guide will help the user in maintaining strong security which is not easier to detect.
1. Detecting Touch ID and Unexpected Patterns
It is important to avoid any critical or sensitive situation like this and for that, always observe your iPhone and keep on identifying the potential threats that might appear in any way. Biometric security is important to check every single day since it will easily assist you in managing the security of the phone. Alterations in these patterns will alert you of any suspicious activity due to which you can take early action to safeguard your device.
How to change face ID on iPhone
- Go to Settings
- Setup face ID and hold your device at portrait orientation
- Move your head gently and wait for the circle to complete
- Finish face ID scan and hit Continue
- Complete the circle move your head for a second time and Click Done
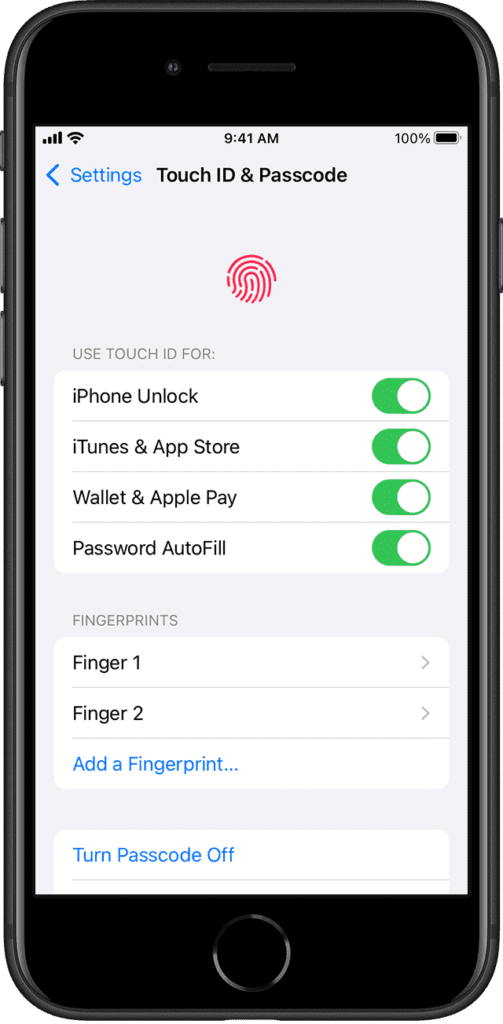
How to change fingerprint security on iPhone
- Open the settings
- Tap touch ID or Passcode
- Enter your passcode
- Delete existing fingerprint
- Tap Add finger print
- Follow the on-screen instructions to complete the process
2. Two-Factor Authentication
It is one of the most important security features that will protect your system from any external threat. Due to its vigilant system, the user gets an extra layer of protection which stops unauthorized access and makes sure that the verification steps are completed smoothly rather than direct access to anyone trying to sign into your phone.
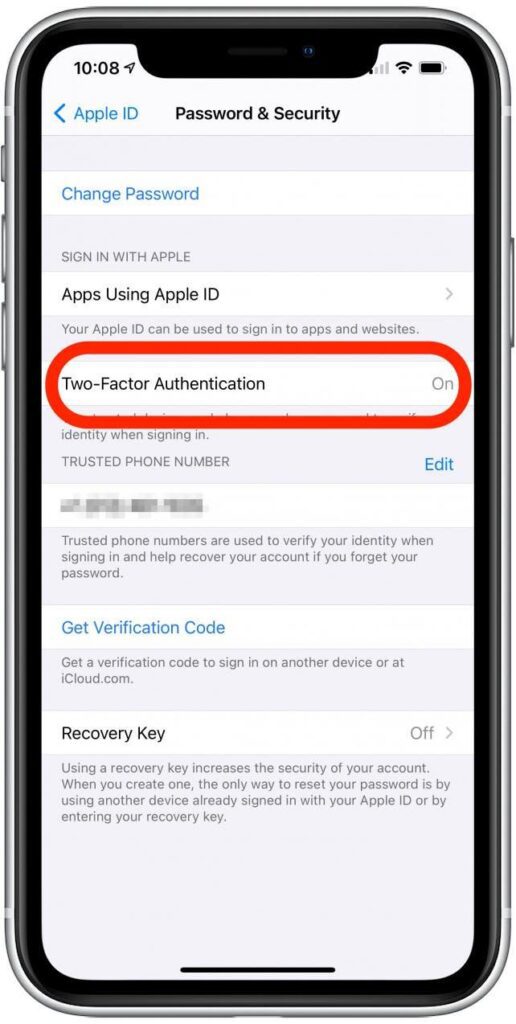
How to turn on Two-factor authentication
- Go to Settings > iCloud > iCloud profile name > Password & Security
- Toggle on two-factor authentication
- Select your country and enter your phone number
- Type in the code you received on your phone
- Now enter your Apple ID and password
3. Analyzing Apple ID
Analysis of your Apple ID is important and it is due to you to take good care of your device’s security. Regularly analyze the security features which will also allow the users to stop any sort of unidentified activity as well as block the requests that are coming from unauthorized servers. These issues are reported to Apple and they take strict action against them.
4. Installed Applications Security Check
Analyzing your installed applications is also important since a threat might come from an already existing application no matter how safe they are. Any application which is not working optimally and is creating legitimacy issues must be uninstalled and the files downloaded from that application must also be uninstalled.
Remote Access Removal with Additional Security Guides
If a user’s analysis has not observed any different signs or symptoms of hacking, the device is safe at the moment. But if the user has detected something alarming, the user must delete that on the spot and make sure that the device and its files are removed completely from the mobile phone. Similarly, always make sure that your phone is in the hands of a trusted person, and never forget to double-check your phone daily for any hints of iPhone remote accessibility.
Protection against Unwanted Access
One of the most common mistakes users make is that they never change their passwords and always stick to easier passwords since they are easier to manage. But it is always recommended that a password must be a long one with different signs and numbers added alongside a capital and small letters mixture. These sorts of passwords secure your device optimally. Sensitive data must be stored safely and it is recommended not to upload such data on clouds or third-party applications no matter what they claim. Users must follow these practices and steps to ensure they are never compromised and always secure. Similarly, always avoid clicking on unwanted or unidentified links that you receive on any social media or messaging application.
FAQs on Remote Access
● How can I handle security risks for safeguarding my iPhone against remote access control?
It is important to go through regular security checkups as well as make sure that there are no unauthorized activities performed on your iPhone. In case you are detecting any sort of risk, you must stop sharing anything with anyone and try to reset on an emergency basis to stop the access. It is better to factory reset your phone but only in that case where all your data is safe.
● How can I secure my iPhone against remote access through applications?
First, the iPhone never allows any third-party application to be installed on your phone. In case you have downloaded such an application, keep on checking the phone’s performance as well as the application’s working since in case of a breach, the application might have a serious performance issue which will indicate that you need to protect your phone from that app. Uninstall all such applications and remove the related or downloaded files too.
FAQs for Identification of Spyware
● How can I recognize spyware or viruses in my iPhone?
There are different signs of such spyware or viruses that they utilize your data excessively, increase the unusual device behavior, and keep on halting the iPhone due to unknown reasons. In this case, iOS must be updated as soon as possible to protect the phone against unwanted bugs or attacks. Similarly, keep on searching the mobile phone for any application that you might not have installed after identification, and delete the application and remaining files from the file manager.
● How can I protect against external hacking?
There are different methods through which you can safeguard your iPhone which are changing your iCloud account passwords at regular intervals, using long and complex passwords, enabling the two-factor authentication on your device, and monitoring the device linking with different other devices. Similarly, never click on external links that are sent from unauthorized access. These might contain any spyware or viruses that might steal your data at once.
Conclusion
In this article, different precautionary steps are recommended for iPhone users to make sure that the device remains safe against any external threats, spyware, and hacking. Remotely accessing iPhones and controlling them is common which must be tackled with different steps and analyzing your device regularly. Always keep checking your phone for potential threats but never forget that you must take care of your things by yourself. We are more than happy to assist you regarding your phone’s security. Surf Safely and enjoy!
Read More:





